I’m always thinking about the damage caused by the disinformation that inundates us every day.
While disinformation comes in many forms, I’m primarily talking about the social engineering tactics designed to con us into divulging valuable data. Whether they result in tangible losses or not, the results can feel criminal to those victimized by them.
As an IT business owner, I have seen these scams cause data loss, login credential theft, financial and reputational harm, and legal hassles, among other things. They reduce efficiency and increase anxiety at work and home.
Worse, however, is the erosion of our ability to TRUST.
The FBI reported that Cyber criminals cost U.S. consumers and businesses approximately $9 billion in 2023, but their most devastating impact might be the theft of our trust in what we read, hear and see in every aspect of our lives.
Emails, texts, phone calls, books, ads, websites, podcasts, articles, social media, streams, pictures, graphics, videos — the proliferation of false information using such communication methods causes us to reflexively fact-check so much of what we consume — unless we know it to be true from personal experience.
Much of our distrust stems from social engineering. For instance, cyber criminals engineer phishing emails, texts and phone calls to try to trick us into handing over our Personally Identifiable Information, or login credentials to email, financial, healthcare, public utility, government, social media and other online accounts.
Social media, particularly X (Twitter), Facebook and Tiktok, contribute greatly to the loss of our trust, too. The onslaught of false memes and posts threatens to turn right and wrong upside down.
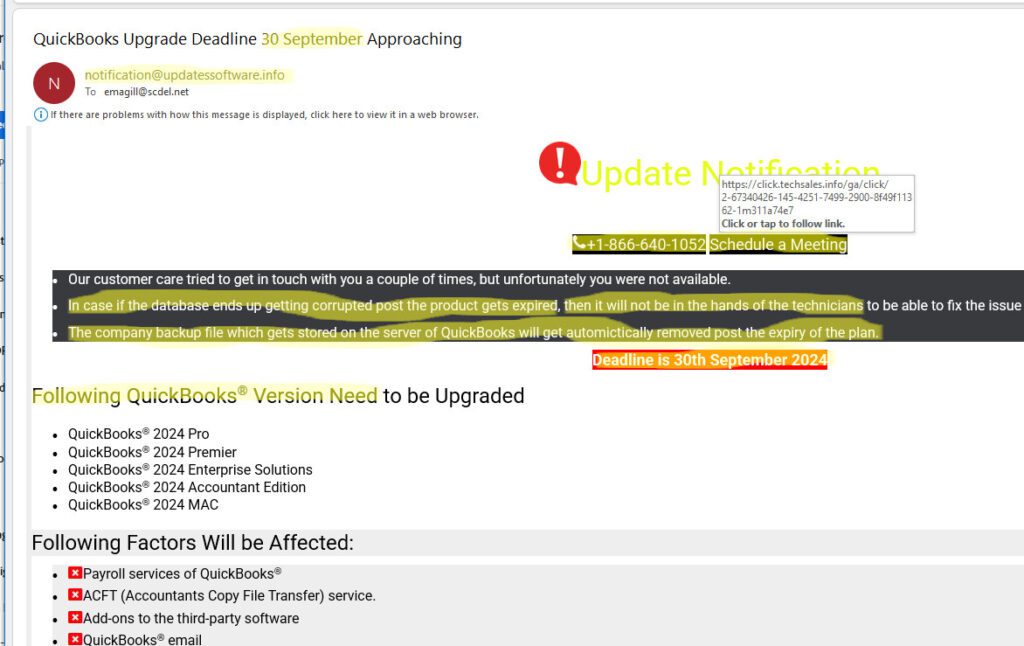
I receive calls and emails from clients every month trying to determine the legitimacy of fake email invoices from brands such as Norton or Quickbooks, extended warranty offers on their car or from Dell, text messages inquiring about a property for sale that they don’t own, or cons preying on their desire to help those less fortunate through donations.
It also gives us pause with good emails, phone calls or texts, as the phish, with the help of AI, look as convincing as legitimate messages. We can become paralyzed trying to decide whether to click or not, whether to open or not, until we get help from another source, such as websites devoted to unmasking scams, or family, friends or colleagues.
It has become so bad that I have customers questioning whether they actually owe payments on invoices with companies that they know they do not do business with.
How do we handle the barrage of this kind of disinformation?
First of all, don’t reply to the email, text, or phone call. I have seen more than one customer, indignant at a fake bill, call the number in the email to dispute it and get burned for thousands of dollars.
Instead, perform due diligence … due diligence … and due diligence.
Whether performing vendor risk assessments, market research, business intelligence, or any other kind of research, or contemplating the legitimacy of an email or text, we must perform due diligence to separate fact from fiction to make sound decisions.
So, be sure to be diligent, and reclaim your ability to TRUST.