Cybersecurity Awareness Month heightens our vigilance in October, but we can’t let our guards down at any time of year anymore, especially during the holiday shopping season.
Small businesses are not likely to be attacked directly by cyber criminals unless you do business with more valuable targets. You will, however, be attacked with the phishing emails that hackers deploy in the hopes that some “fish” will take their bait.
Cyber criminals now use AI writing tools to help make their phishing emails more convincing, too.
You can, however, spot phishing emails by remaining diligent at all times.
My Golden Rules for handling emails:
- If you don’t know the sender, do not click any links or file attachments. Delete the email.
- If the email is relevant to you, go directly to the sender’s website in your browser.
- For well-known brands, hover over the link (don’t click) to see if it goes to the brand’s website (i.e., dell.com versus something.com/dell)
- If you know the sender, but receive an unexpected email from them, do not click links or file attachments until you confirm that the sender you know actually sent it.
- Do this by phone — a hacker could hijack the email account and make it look like the sender you know is providing confirmation.
- If you mistakenly click on a link in an unexpected email, and it takes you to a page to change your password, do not enter your password. Close the page.
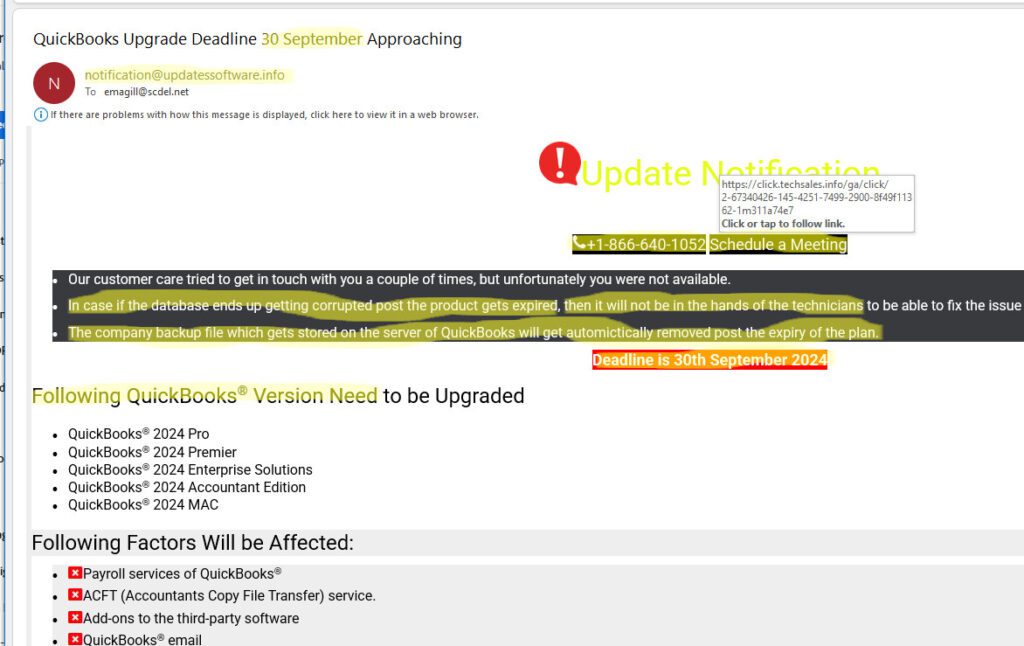
Below is a phishing email that I received that incorporates elements of many phishes:
As you can see, this phishing email:
- Uses the International date format (day / month) versus the month / date format that I would expect in the U.S.
- The From: email address is not @intuit.com or @quickbooks.com. It’s @updatessoftware.info.
- The phone number shows up in searches for known scams.
- Hovering over the link reveals it goes to techsales.info instead of intuit.com or quickbooks.com.
- Awkward language
- The text uses fear tactics by claiming the database will be corrupted and backups automatically removed, preventing recovery, if the deadline is missed.
What would I do with this email?
This email caught my attention because I knew that Quickbooks is requiring desktop software customers to upgrade before Sept. 30 if they want to continue using the desktop software instead of Quickbooks Online.
The International date format, however, gave me pause initially. The fake From: email address sealed it.
Had the hackers spoofed a legitimate Quickbooks email address, the other elements would have still confirmed this as a phish.
You also want to protect your passwords as follows:
- Use a password manager such as one of these.
- Do not send passwords in emails and text messages unless encrypted
- Do not use the same passwords for business and personal use
- Do not store passwords in word processing files or spreadsheets
- Do not share your passwords with anyone, including co-workers
If you want more in-depth information about cybersecurity awareness, you can visit the Cybersecurity and Infrastructure Security Agency (CISA) website at https://cisa.gov.